To do so select the RSA key size among 515 1024 2048 and. RSA-SHA384 is an RSA signature of an SHA384 hash.

Cnit 221 Security Module 5 2 Ver 2
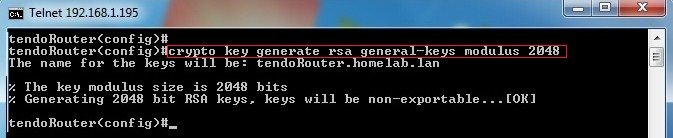
Configure Ssh On Cisco Router Lazy Geek
Terminals Worldline Com
RSA-SHA256 is an RSA signature of an SHA256 hash.

Crypto generate rsa key. Crypto key generate rsa general-keys label tokenkey1 storage usbtoken0. KeyObject objects are not to be created directly using the new keyword. RSA Cryptography Demo - more complete demo of RSA encryption decryption and key generation.
The algorithm capitalizes on the fact that there is no efficient way to factor very large 100-200 digit numbers. These extensions are consistently identified by prepending names with the node. For ECDSA or ECDH.
Openssl genrsa -out privatepem 1024 generate private key file openssl rsa -in privatepem -text view info in the private key file openssl rsa -in privatepem -pubout -out publicpem extract public key to file openssl rsa -in publicpem -pubin. Pass an EcKeyGenParams object. Openssl rsa -pubout -in private_keypem -out public_keypem Extracting the public key from an.
RSA encryption usually is. DSA EC crypto keys have same feature. That means that if you have a 2048 bit RSA key you would be unable to directly sign any messages longer than 256 bytes long and even that would have problems because of lack of padding.
For instance the nodekeyObject key format can be used with the subtleexportKey and subtleimportKey methods to convert between a WebCrypto. To generate a key pair select the bit length of your key pair and click Generate key pair. The cryptocreateSecretKey cryptocreatePublicKey and cryptocreatePrivateKey methods are used to create KeyObject instances.
The original specification for encryption and signatures with RSA is PKCS 1 and the terms RSA encryption and RSA signatures by. RSA-SHA1 is an RSA signature with an asymmetric key pair of an SHA1 hash. Routerconfig crypto key generate rsa label MYKEYS redundancy.
Openssl rsa -in pathtoencryptedkey -out pahttodecryptedkey For example if you have a encrypted key file sslkey and you want to decrypt it and store it as mykeykey the command will be. The algorithm closely follows NIST FIPS 186-4 in its sections B31 and B33. Generate an ECDSA SSH keypair with a 521 bit private key.
The name for the keys will be. Inspecting the output file in this case private_unencryptedpem clearly shows that the key is a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----. This is useful for encrypting data between a large number of parties.
The valid values for algorithmName are RSA RSA-SHA1 RSA-SHA256 RSA-SHA384 RSA-SHA512 ECDSA-SHA256 ECDSA-SHA384 and ECDSA-SHA512. It is also one of the oldest. Usage Guide - RSA Encryption and Decryption Online.
Pass an HmacKeyGenParams object. You can use the openssl command to decrypt the key. The generated private.
In the first section of this tool you can generate public or private keys. The Nodejs Web Crypto API extends various aspects of the Web Crypto API. That changes the meaning of the command from that of exporting the public key to exporting the private key outside of its encrypted wrapper.
The Rivest-Shamir-Adleman RSA algorithm is one of the most popular and secure public-key encryption methods. Crypto key generate rsa crypto key generate rsa. Algorithm is a dictionary object defining the type of key to generate and providing extra algorithm-specific parameters.
The modulus is the product of two non-strong probable primes. RSA is a single fundamental operation that is used in this package to implement either public-key encryption or public-key signatures. Ssh-keygen -t ecdsa -b 521 -C ECDSA 521 bit Keys Generate an ed25519 SSH keypair- this is a new algorithm added in OpenSSH.
Openssl genpkey -algorithm ed25519. Perform the signature verification operation defined in Section 82 of with the key represented by the internal slot of key as the signers RSA public key and the contents of message as M and the contents of signature as S and using the hash function specified in the hash attribute of the internal slot of key as the Hash option for the EMSA-PKCS1-v1_5 encoding method. RSA Encryption Demo - simple RSA encryption of a string with a public key.
For AES-CTR AES-CBC AES-GCM or AES-KW. Cisco IOS Security Command Reference. RsaCtfTool Usage Uncipher file Print private key Attempt to break multiple public keys with common factor attacks or individually- use quotes around wildcards to stop bash expansion Optionaly send the results back to factordb Generate a public key Dump the parameters from a key Check a given private key for conspicuousness Factor with ECM when you know the approximate length in digits of a.
Only one key pair per person need exist. Choosing a key modulus greater than 512 may take a. RSA RivestShamirAdleman is a public-key cryptosystem that is widely used for secure data transmission.
Commands A to C Cisco IOS XE Release 3SE Catalyst 3850 Switches 8 crypto key generate rsa crypto key generate rsa. Import Crypto from CryptoPublicKey import RSA from Crypto import Random random_generator Randomnewread key RSAgenerate1024 random_generator generate public and private keys publickey keypublickey pub key export for exchange encrypted publickeyencryptencrypt this message 32 message to encrypt is in the above line. Crypto key generate rsa Author.
Pass an RsaHashedKeyGenParams object. RSA Generate Keys. Pass an AesKeyGenParams object.
The acronym RSA comes from the surnames of Ron Rivest Adi Shamir and Leonard Adleman who publicly described the algorithm in 1977An equivalent system was developed secretly in 1973 at GCHQ the British signals intelligence agency by the English. Visually Inspect Your Key Files. This is an online tool for RSA encryption and.
As we discussed above the public key generated is in X509 format and we use public key for encryptionHence we need X509EncodedKeySpec class to convert it again to RSA public keyRemember that we have base64 encoded public keysHence first let. Crypto key generate rsaコマンドの利用例は以下の通りです Ciscoconfig crypto key generate rsa The name for the keys will be. In contrast a cryptographical hash can take an arbitrarily long message and compress it into a short string in such a way that we cannot find two messages that hash to the same value.
MYKEYS Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. The following decrypts it. Back In RSA we might receive a Base64 encrypted message and we have a private key.
The following example specifies the redundancy keyword. For RSASSA-PKCS1-v1_5 RSA-PSS or RSA-OAEP. CryptoPublicKeyRSAgenerate bits randfuncNone e65537 Create a new RSA key pair.
Must be RSASSA-PKCS1-v1_5 Nodejs-specific extensions. Ssh-keygen -t ed25519 Extracting the public key from an RSA keypair. Most applications should consider using the new.
String The algorithm name. This tool generates RSA public key as well as the private key of sizes - 512 bit 1024 bit 2048 bit 3072 bit and 4096 bit with Base64 encoded. RSA is widely used across the internet with HTTPS.
RSA and ECC in JavaScript The jsbn library is a fast portable implementation of large-number math in pure JavaScript enabling public-key crypto and other applications on desktop and mobile browsers. Nodejs uses a KeyObject class to represent a symmetric or asymmetric key and each kind of key exposes different functions. With a given key pair data that is encrypted with one key can only be decrypted by the other.
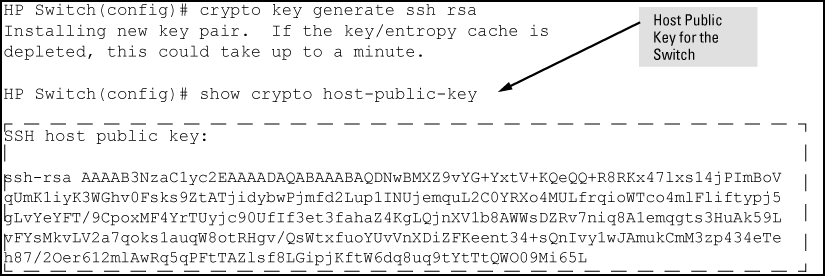
Configuring The Switch For Ssh Operation

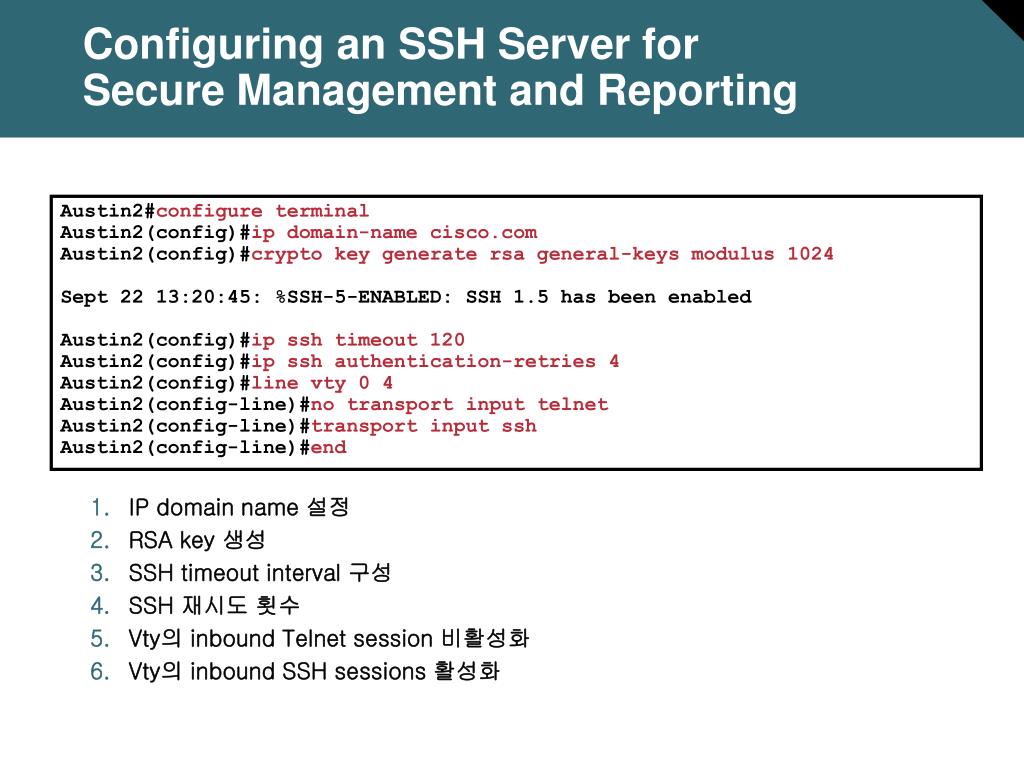
Configuring An Ssh Server For Secure Management And Reporting Scnd
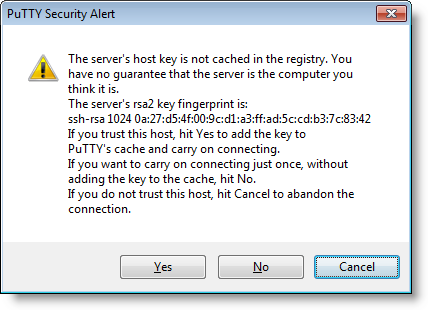
Calculating A Ssh Fingerprint From A Cisco Public Key Didier Stevens

Ken Felix Security Blog Building Exportable Keys And Exporting Via Cisco Ios
Cisco Router Generate Rsa Key 1024

Cisco Asa Ver 6 7 And 8 2 Generate Rsa Certificate Keys Youtube

Packet Tracer Crypto Key Generate Rsa Brownrite
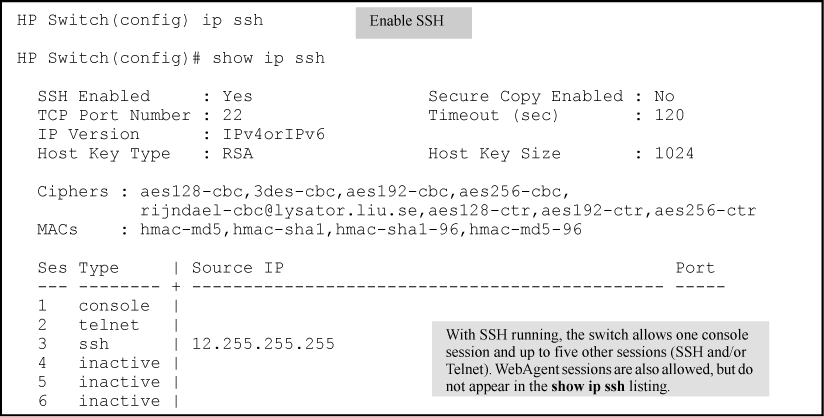
Configuring The Switch For Ssh Operation
